Despite the constant warnings given to companies to comply with data protection standards, data leaks are still common. Besides, hackers are increasing the complexity of their attacks which can leave unprotected companies in a much more vulnerable situation. In the past ten years, the USA has registered 9,750 data breaches which resulted in the theft of more than 1,270 million data records.
A recent credit card data leak in the USA affected major players in the travel industry including Expedia, Booking.com, and Hotels.com, resulting in the theft of payment information (including CVV), addresses, names, and ID numbers from more than ten million clients. The company responsible for the reservation system had been storing unprotected credit card information for years and, evidently breaching the Payment Card Industry Data Security Standards (PCI DSS).
Obtaining PCI DSS certification becomes especially important to prevent data security from being compromised as we move towards a cashless society. In times of a global pandemic where customers are flocking to online channels for shopping, card-not-present payments have increased and so has fraud.
Cardholder data security is now a primary concern for both businesses and customers. Ensuring it is the tricky part.
PCI DSS and The 12 Requirements for Data Protection
To guarantee consumers’ credit and debit card data security, the major payment card networks got together back in 2006—58 years after IBM created the first credit card with a magnetic stripe — to discuss and define worldwide measures. The group was originally formed by American Express, Discover, JCB International, MasterCard, and Visa Inc. and was given the name of Payment Card Industry Security Standards Council (PCI SSC).
PCI SSC created a set of regulations, the PCI DSS requirements, to be followed by anyone involved in storing, processing, or transmitting cardholders’ data. If you’re a merchant accepting card payments, you’re obliged to follow the PCI DSS requirements to ensure this information is securely protected.
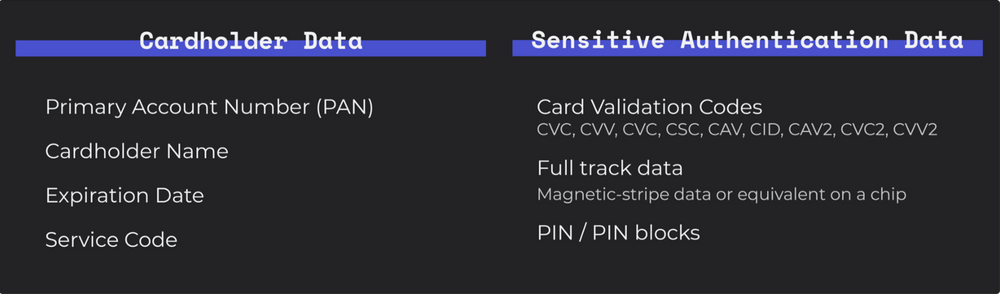
Organizations are allowed to store cardholder data. Sensitive authentication data, even if encrypted, is completely prohibited from being stored.
The latest version of PCI DSS requirements, version 3.2.1, was released in May 2018. The twelve PCI DSS requirements are divided into six control objectives and can be explained as follows:
Build and maintain a secure network
1. Install and maintain a firewall configuration to protect cardholder data:
Firewalls work as security barriers between trusted networks and untrusted networks. They prevent external users from accessing private information like payment card data.
2. Do not use vendor-supplied defaults for system passwords and other security parameters: Default passwords are relatively simple to access by the general public and even more for experienced hackers. You should always change them and delete, or deactivate, unnecessary user accounts. As a good practice, you should activate 2-factor authentication for every login.
Protect cardholder data
3. Protect stored cardholder data:
If you need to store cardholder data, you have to ensure that it’s encrypted, unreadable, and unusable for other people, rather than for cardholder operations. Also, you should never pass it through unsafe channels, like email or chat.
4. Encrypt transmission of cardholder data across open, public networks:
Whether it is the internet, wireless technologies (such as Bluetooth), satellite communications, or cellular technologies, whenever you need to use them to pass confidential information, make sure you follow strong cryptography and security protocols.
Maintain a vulnerability management program
5. Protect all systems against malware and regularly update anti-virus software or programs:
Malware, a short word for malicious software, can cause damage to your network during simple work activities, such as the use of the internet, managing storage devices, and sending emails. Anti-virus software, or programs, work to detect, remove, and protect against these threats.
6. Develop and maintain secure systems and applications.
Even the most secure systems can have vulnerabilities. Therefore, it’s a good practice to periodically test for these exposures and create risk standards to evaluate each one.
Implement strong access control measures
7. Restrict access to cardholder data by business need to know:
“Need to know” refers to data that is required to perform a task. Access to this data should be restricted on permissions to avoid leaks and to keep it unavailable to unauthorized personnel.
8. Identify and authenticate access to system components
Assign a unique identification to every user to ensure you can trace each user’s actions in the system. With a unique ID, you can give users accountability for their actions. Also, avoid allowing unnecessary permissions. While the finance department might need access to accounting data, a tech engineer will need access to API keys.
9. Restrict physical access to cardholder data
If your organization uses physical places to store cardholder data, such as data centers, server rooms, or any other facilities for the same purpose, all of these should be protected accordingly. Besides restrictions, some measures comprise the use of security cameras and access control systems to monitor the physical access to these centers.
Regularly monitor and test networks
10. Track and monitor all access to network resources and cardholder data:
One key metric to identify and prevent access to network resources and cardholder data is the track of user data done through system activity logs, which reports user activity and security information to authorized personnel.
11. Regularly test security systems and processes:
Sometimes new software comes with new vulnerabilities. Test your systems and processes for security check and update them accordingly to avoid exposures. Tests can be performed with wireless network scans, network access control, and wireless IDS/IPS, for example.
Maintain an information security policy
12. Maintain a policy that addresses information security for all personnel:
Apply policies that establish security standards for the whole company and employees. Revise the security policies regularly and share them with all company workers. Besides protecting cardholder data, PCI DSS certification provides you with mechanisms to avoid expensive data breaches.
The Steps to Become PCI DSS Compliant
Merchants, gateways, payment service providers (PSPs), or acquirers should consider the following steps to become PCI DSS compliant.
Identify the scope of PCI DSS in your business.
The first thing you should do is to identify which systems must be tested for PCI DSS compliance. Consider all the people, processes, and technologies that process, store, and collect cardholder data or sensitive authentication data and include it in the scope. You should take this step not only the first time you plan to become compliant with PCI DSS but every year before the PCI DSS annual assessment.
The steps to take for the PCI DSS assessment depend on your level of compliance. Each payment brand — Visa, MasterCard, Discover, American Express — has its own specifications for each level, but they all share some guidelines:
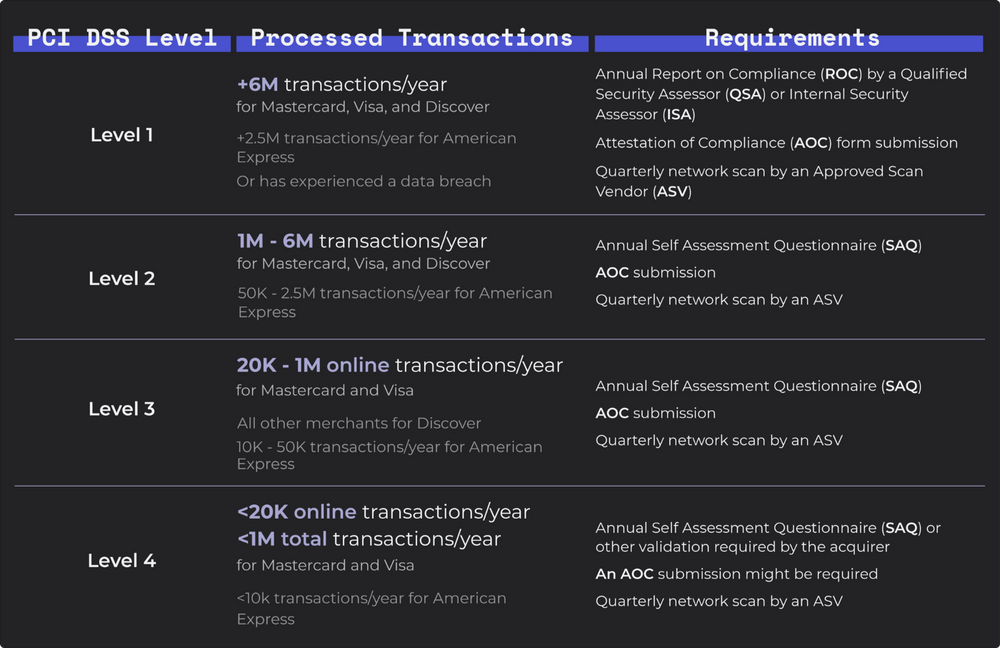
Perform the PCI DSS assessment of your environment.
Assess your PCI DSS scope — people, processes, and technology — and check if the company is following each of the requirements properly. Work with IT and security departments to ensure the right security configurations and protocols are in place. On the official PCI SSC document library, you will find some resources to support you on each step. Depending on the level of PCI DSS above you will have to fill a Self-Assessment Questionnaire or require a qualified auditor to submit a Report on Compliance:
The SAQ (Self-Assessment Questionnaire). This document works as a self-assessment tool for your level of compliance. When filling the SAQ, you’re checking if the company follows the PCI DSS requirements. According to organization type, you’ll have to prepare different SAQ.
- SAQ A: for merchants who accept card-not-present payments (e-commerce or mail/telephone orders) and who’ve outsourced to a third-party entity the functions of storing, processing, and transmitting cardholder data. Not applicable to face-to-face payment channels.
- SAQ A-EP: applies to e-commerce merchants that, although they’ve outsourced all the processing of cardholder data to a PCI DSS validated provider, their website can impact the security of the payment transactions.
- SAQ B: for merchants with imprint machines and/or standalone dial-out terminals, both not storing cardholder data.
- SAQ B-IP: applies to merchants who use standalone PTS (PIN Transaction Security) approved payment terminals that don’t store cardholder data, but which have an IP connection to a payment processor.
- SAQ C-VT: for merchants who outsource the cardholder data storage to a PCI DSS certified third-party and which use virtual payment terminal solutions — web-based terminals — that require manual entering of cardholders’ data.
- SAQ C: for merchants who have their payment application systems connected to the internet and who don’t store cardholders’ data.
- SAQ P2PE: point to point encryption works for merchants who don’t store electronic cardholder data, and who use hardware payment terminals from a PCI SSC listed company.
- SAQ D: applies to all other merchants and service providers that process payment data.
On the 18th page of this PCI DSS document, you can determine which is the SAQ that best applies to your organization environment.
The ROC (Report on Compliance). A summary of evidence of the company’s compliance condition for each PCI DSS requirement. The ROC is completed by a qualified security assessor (QSA) who must detail all the records of assessment activities to verify that the company is compliant with PCI DSS. After the audit, the QSA submits the document to the merchant’s acquirer who later sends it to the card network for verification.
Quarterly Network Scans. As part of requirement eleven, organizations must complete vulnerability scans performed by an Approved Scanning Vendor (ASV). These scans must be performed quarterly and after significant network changes.
Complete the Attestation of Compliance (AOC).
The Attestation of Compliance is completed by a QSA or a merchant’s internal qualified auditor and it serves as a declaration of the merchant’s compliance status with the PCI DSS. You can find the AOC template destined for merchants or service providers on the PCI SSC document library. Submit the required documentation.
You should submit the SAQ to your acquirer or the card network. The QSA submits the ROC and AOC to the acquirer or the card network. After submission, you might be asked to prepare other documents or revise the ones you have sent with an updated report.
Reassess your PCI DSS compliance periodically.
To keep PCI DSS compliance, every entity has to do a new validation every year and complete and submit the necessary documentation. But this is also a continuous process: organizations need to reassess their PCI DSS compliance every time there’s a new update involving payment card data like moving physical business to online, or adding a new customer support service, or whenever there’s a new update on the PCI DSS requirements.
The Costs of Becoming PCI DSS Compliant
The costs to become PCI DSS compliant and to maintain the certification through the years depend on the level of compliance of your organization but also on your organization’s setup:
- Business Size. Larger organizations need to manage more processes, technology, staff, and cardholder data which means there’s more potential for compliance gaps.
- Required training and policies. The staff who handles cardholder data needs the required training. In some cases, organizations need outside assistance to help employees understand and respond to needed requirements. Every new employee can increase the costs of training or require more elaborate policies and procedures.
- Network environment. The way your organization’s network is designed can affect PCI DSS compliance costs. Network segmentation can help you reduce some of the associated costs. By isolating the cardholder data environment from the remainder of your company’s network you reduce the scope and cost of PCI DSS assessment, the cost and effort of maintaining the PCI DSS controls, and the organization’s risk. The cardholder data is consolidated into fewer and more controlled locations and can’t communicate with external networks. For example, in a flat network (no network segmentation) with 100 servers, all the servers are open to audit scope. Supposing that only 4 servers contain cardholder data, by isolating these servers into a segmented network you would reduce the scope of PCI DSS assessment by 96%.
Level 1 merchants would generally pay the higher costs due to necessary requirements of QSA audits, adding the quarterly vulnerability scans, penetration testing, policies development, and software and hardware updates.
If you are wondering about the expenses associated with PCI SSC qualification and training programs you can check the PCI SSC program fee schedule list.
Implications of Being Non-Compliant With PCI DSS
Beyond being exposed to data breaches, companies that don’t follow PCI Compliance face difficulties in closing deals with acquirers and payment processors. There are further risks to take into consideration for those who fail to follow PCI DSS compliance:
- Excessive fines, legal charges, and penalties. In the case of a data breach, the PCI SCC establishes fines ranging from $5,000 to $100,000 per month depending on your degree of non-compliance. For each cardholder information that has been endangered, the merchant is penalized with $50 to $90. In 2017, Target announced a total cost of $202 million regarding a data breach that happened in 2013 and which compromised payment data of 70 million people. The expenses included all legal fees and other data-breach related costs.
- Compensation costs. Besides all the legal costs you’ll have, and if you want to keep your company in the market, you’ll need to compensate your customers after a data breach with credit card monitoring and identity theft insurance.
- Revenue loss. If your company is affected by a data breach, the press will make sure to point out the issue and warn consumers to take protective measures. Your business can find itself in a vulnerable situation with clients moving away and filing lawsuits against the company. Besides a damaged public image, your business might face a plummet in sales. Target’s profit declined by 30% in the year of its data breach.
- Cancellation of card payments acceptance. Your acquirer might choose to ban you from accepting card payments.
- Additional audit requirements. Depending on its location and on how big the company is, you can start being audited by regulators such as the Federal Trade Commission (USA) or the Data Protection Authority (Europe). These audits might present additional fines.
The costs of becoming PCI DSS compliant and maintaining the certification are minimal when compared to the inconveniences of being non-compliant. Don’t risk any of your customer information, your organization’s reputation, and revenue because of PCI DSS costs. You should never accept payments if you’re not sure you can keep cardholder data secure.
How Switch Helps You Minimize the PCI DSS Burden
Switch can help minimize significantly the PCI burden for companies that integrate with our Dynamic Forms, Hosted Checkout. Our Hosted Checkout and Dynamic Forms use a hosted payment field that redirects customers from your cart to our checkout. When it’s time to pay, the customer enters their payment information into our hosted payment field originated directly from our PCI certified servers. Because the payment information never communicates with your website and network, you significantly reduce your PCI DSS scope.
Another form of reducing your PCI DSS scope is through the Switch Vault which allows the tokenization of payment parameters. With tokenization customers’ payment details are protected in a PCI DSS compliant manner. By replacing payment card data with a token, you place another obstacle between your business and fraudsters because the card data becomes entirely inaccessible to third party entities.
To ensure that all types of threats, attacks, and suspicious activity are closely monitored and that your transactions are secure we’ve created six main security principles:
- Secure network and systems. Software updates, firewalls, monitoring, logging, alerting;
- Safety of cardholder data. Hashing, encryption, anonymization, restricted access to servers, storage, and networks;
- Vulnerability management program. Intrusion Detection System (IDS), Systems Integrity Monitoring (e.g. FIM), risk assessment, anti-virus, high-quality standards in software development and developers training;
- Access Control. Restrict users’ access, track users’ access, restrict physical access;
- Information Security Policy. Clear processes and policies communicated to all staff who work at Switch.
Switch’s security approach provides organizations a way to reduce the risk of a potential data breach while reducing the time-consuming and costly process to achieve PCI DSS certification. Our security department works every day to keep your integrations and transactions secure so you can keep focusing on business-as-usual.
Although you can choose to shift some activities related to cardholder data protection you’re not fully free from undergoing a PCI DSS assessment in your organization.
If your business accepts card payments, it is still your organization’s responsibility to comply with PCI DSS. You need to prove that your organization is compliant with the requirements, confirm that your payment providers are also compliant with PCI standards, and repeat the assessments every year and whenever there are changes in requirements.
If you’re at the start of your PCI DSS compliance journey, we recommend you first take a look into the current and future needs of your organization. Identify all the people, processes, and technologies that are involved in the activities of processing, storing, and transmitting cardholder data and decide which changes and strategies can be implemented internally. Afterward, understand which elements will need external help to achieve your compliance needs and research the adequate providers.
Reach out to us, if you find that Switch can be the right fit to help your organization achieve its PCI DSS compliance needs.